Background
How the machine worked
Breaking the code
The Enigma simulator
Let’s give it a go
Warning
Downloading the app
Known problems
Resources
Background of the Enigma coding machine
Before and during the Second World War the German military communicated using the Enigma encryption machine. The sender used the machine to convert plain German into apparent gibberish and the receiver could only convert it back to plain German if the correct settings were used. The Germans thought the machine to be unbreakable because it has 10^23 settings, in modern terms this would be called 77-bit encryption. That sounds like a lot – and it is! The encryption of an internet connection is usually 16 or 32 bit. Still, the Enigma was cracked… even before the war broke out.
Polish mathematicians found a way of cracking the code and just before the Germans invaded Poland their knowledge was transferred to the British. Alan Turing and others helped improve a Polish design for an electronic machine that could automate the cracking (the same Turing en passant invented the computer). This made it possible to read the instructions for the German U-boats and change the routes of convoys travelling from the US to the UK, saving thousands of lives. After the war Churchill said the code breakers shortened the war by two years.

Photograph of an Enigma machine, taken in the
National Cryptographic Museum by Austin Mills
It is an inspiring story about a problem of massive complexity directly affecting the lives of thousands of people and the course of the war. It is a war story were human willpower is used to save people, not to make more destructive bombs. But it is also a dramatic story of people who were not allowed to say what they were doing for the war effort. It took until 2009 before the British government gave out a medal to the veterans, saying “We also served”. And Alan Turing? He was driven to suicide by the British government because of his homosexuality…
How the Enigma worked
The photo above shows an actual Enigma machine, the figure below shows a schematic overview. In both cases, from the bottom to the top we see a plugboard, some keys and some letters that can light up. At the top of the machine there are some rotors, in the photo these are hidden under the black cover.
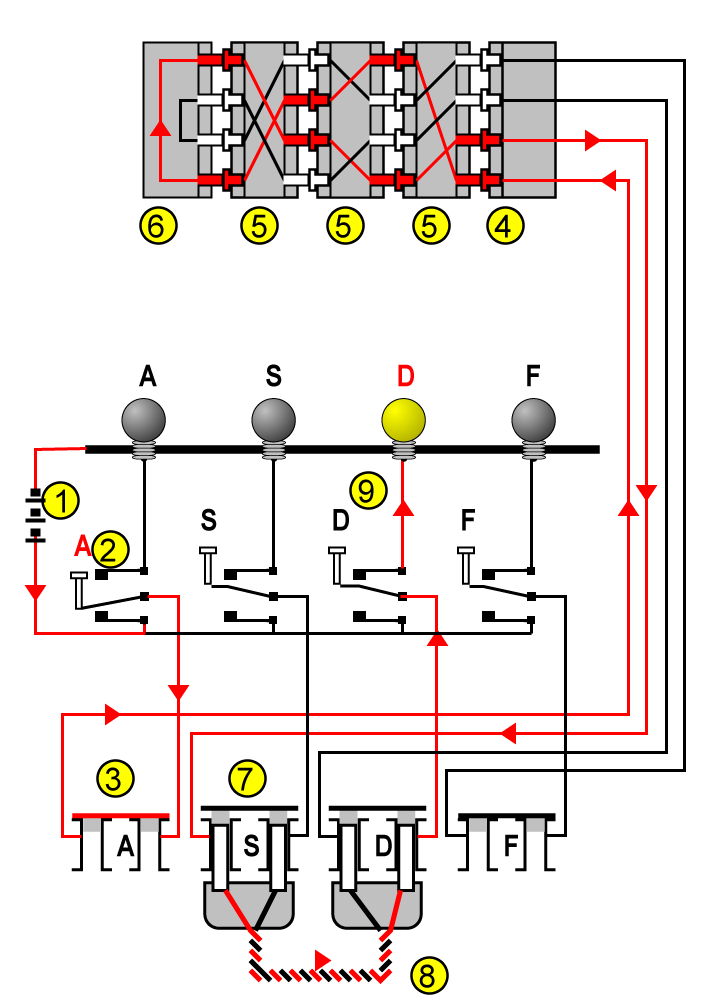
The wiring inside the Enigma machine. Figure adapted from Wikipedia
To see how the encryption works we’ll press a key in the figure below, let’s say “A”. The circuit closes (#2) and the signal goes through the plugboard (#3), which is not connected. The signal then goes to the entrance wheel (#4) and into the rotors (#5). The rotors have 26 contacts on each side and are wired in a certain pattern. If the signal enters at contact 1, it exits at contact 5, if it enters at contact 2, it exits at contact 19 (for example). The signal is scrambled three times (there are three rotors). The reflector (#6) is a sort of rotor, but with contacts on only one side. The signal goes another three times through the rotors and is now thoroughly scrambled and the “A” has become an “S”. The signal goes to the plugboard again, where the “S” is connected to the “D” (#7 and #8). Finally, the letter “D” lights up.
Until now it looks like a complicated way of scrambling letters. The key of the machine is in the rotors which, not surprisingly, rotate. After a key press the right motor would move a position. After a full turn (i.e. 26 letters), the middle rotor would move a position. When that has made a full turn it would move the left motor one position. The consequence is that the way the letters are scrambled changes with every key press. Pressing “A” three times will result in three completely different circuits through the machine (which doesn’t mean that there are three different letters, that depends on the circuit).
Depending on the type, the Enigma had three or four rotors and there was a choice between eight different types. A daily code book tell the operator which rotors to use and the begin setting. This is however not enough to get an astronomical 10^23 settings. This is why the military versions included the plugboard. It turns out that 10 cables gives mathematically the most combinations.
Of course, the message has to be decoded again. Thanks to the reflector the machine is entirely reversible. This means that if we had pressed a “D” in the example, we would have gotten an “A” as the result. The only thing needed was to set up the machine on the receiving end to exactly the same setting as the machine of the sender.
Breaking the code
I don’t want to spend too much time talking about breaking the code, but here is the very short version. The key weakness of the Enigma is that a letter will never encrypt to itself. An “A” in plain German will never show up as an “A” in the code. You can use this if you have an idea what the plaintext contains. The content of weather reports are for example predictable. The Germans were also predictable: some operators always opened with “Sehr Geehrter Herr Oberkommandant” or finished with the same salutation. The English also sometimes helped luck a bit: they would lay some sea mines at a particular spot, which was then duly reported by the Germans.
The Enigma simulator
The app does not resemble the original Enigma’s in any shape or form, but the functionality is the same.
- In the box upper left box you can type or copy-paste your message
- The encoded message will be shown in the upper right box
- Between these two boxes you can set the rotor (I-VIII) and reflector types (B or C) and the ringstellung.
- Below this you can set the rotor positions
- In the middle you find the plugboard. You can drag the black lines at the bottom to the circles below the letters to make connections. If a connection is made, it will snap into place, if not, the connector will go back to the bottom.
- Not shown on the screenshot are the buttons “Store”, “Load” and “Defaults”, right of the plugboard. These buttons will store the current rotor settings so you can load them later on. The plugboard settings are not stored, nor is the input message. “Defaults” will refer to the default setting. It will overwrite the stored settings.
- The bottom text box is the “internals field” and shows how the message gets encoded or decoded in the machine. The three-letter groups at the beginning are the rotor positions before and during the encoding (the rotor rotated after hitting the key but before the signal went through them). Then you see the letter you typed. The W shows what the plugboard (or wireboard) did. The numbers 1, 2 and 3 are the rotors (1 is the right rotor). The U is the reflector (Umkehrwalze). The signal goes back through the rotors and the plugboard and the final letter is the en/decoded message.
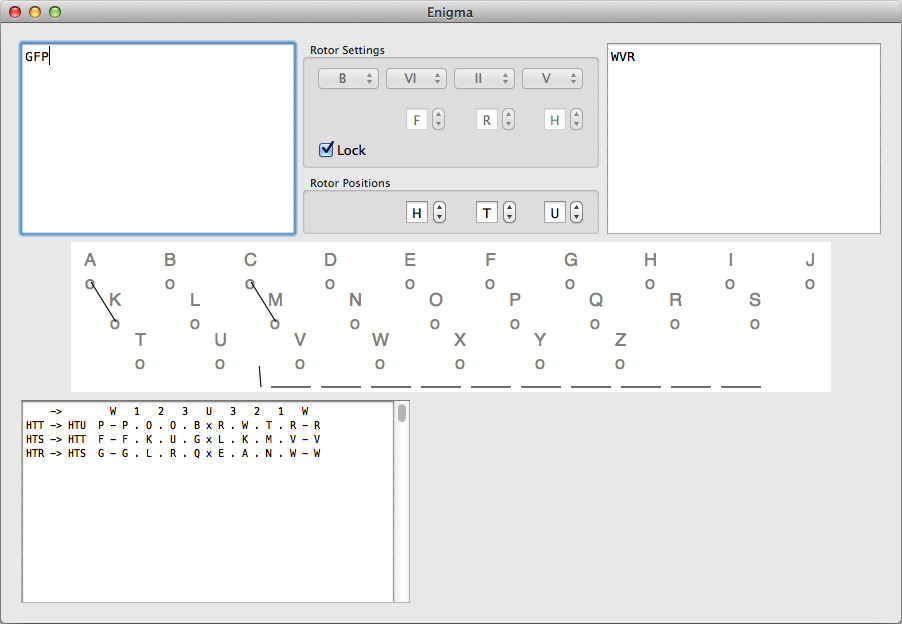
Screen shot of the Enigma app
Let’s give it a go
At the beginning of the day German Enigma operators set up the machine according to the settings of the day. This included three things.
- Set the rotors, choose between the different types (I-VIII). You can also choose a reflector (B or C).
- Set the ringstellung, or offset. These are the letters below the rotors.
- Set the plugboard.
How the individual messages were handled depended on the department and changed during the war. The explanation below is one particular method.
Set the “Rotor Settings” and plugboard as indicated in the table below (also see the screen shot).
| Day | Rotors | Ringstellung | Connections | ID |
| 1 | B-VI-II-V | F-R-H | AK-CM | JWK ONS QKC |
Click the “lock” button to prevent accidental mistakes.
This is the message:
HTR GFP
EONSF VPTJC XBXSP TCMEH MKDHL
UBJJU VBKFT ZBRVE QPKBG EZRZY
KKVAB
- The first triplet
HTRin the code is the rotor position, set this. - Then type in the second triplet
GFP, resulting in the outputWVR. This is the state of the screenshot. - Set the rotor positions now to
WVR - The first quintet contains one of three ID codes (
ONS, see table). This was used to make it easier to communicate over different time zones. This quintet has to be skipped. - Copy-paste the message WITHOUT the first quintet in the input box.
- You can see the decoded message in the right hand box. Congratulations!
Warning
I don’t have access to a real Enigma. I tried my algorithm on example codes and compared the results with other simulators. I think it works correctly… but I can not give any guarantees.
Downloading the app
The app can be downloaded below. The app should work on OS X 10.5 and above, although it was only tested on 10.7 and 10.8. If you find problems, please contact me.
Versions
| Version | Comments |
| 0.1.7 | Added support for OS X 10.5 and 10.6, although I’m unable to test it. |
| 0.1.6 | The current rotor type and ringstellung are now also shown in the internals field. |
| 0.1.5 | Made improvements to plugboard. The wires will now snap into a connector or go back to their original position. |
| 0.1.4 | Implemented defaults and a way of storing them. It is not implemented yet for the plugboard. |
| 0.1.2 | Solved a bug with the rotor increment system |
| 0.1.0 | Improved the plugboard with better colors and connectors. Added an icon |
| 0 | First version |
Known problems
- The plugboard does not recognize changes (so if you want to change AK into AB, it will remain AK, even though the plugboard says AB).
Resources
Invaluable resources for making the app were the following websites:
- Dirk Rijmenants Enigma website contains a wealth of material about the history, the technique etc. It includes a Windows-based simulator.
- A web based Enigma simulator.
- Terry Long’s Enigma simulator for Mac is hands down the most beautiful simulator I worked with (I don’t know about the Windows one)
- This video was actually the direct reason to start writing my code.
- Simon Singh wrote “The code book” about, you guessed it, encoding, decoding and code cracking.
- Peter Wright was a spy at MI5 who after his retirement wrote “Spycatcher”, a controversial memoir that exposed more than the British government wanted. He has been called a hero, a double agent and an asshole, but his book “The Encyclopaedia of Espionage” was the first time I heard of Enigma. I was fascinated and literally read the book to pieces.